Web Application Security 2025: Top Best Practices and Comprehensive Guide

Share This Article
Table of Contents
Subscribe to Our Blog
We're committed to your privacy. SayOne uses the information you provide to us to contact you about our relevant content, products, and services. check out our privacy policy.
What is Web Application Security?
At its core, web application security focuses on ensuring that web applications are guarded against potential threats and cyber-attacks. In a world where we increasingly rely on online platforms for almost everything - from shopping and banking to communication - having secure web applications is no longer optional; it's a must.
Why is Web Application Security So Important?
Every day, numerous online threats target web applications. Some aim to gain unauthorized access, while others seek to disrupt service or steal sensitive data. The consequences of a successful attack can range from financial losses and damaged reputation to severe legal implications.
In the quest to create the next big online platform or to provide the best online service, one must not forget that security is a foundational component. It's not just about protecting the company's data or assets. It's about preserving user trust and ensuring the digital safety of countless individuals who interact with web applications daily.
A great-looking and well-functioning web app is excellent. But, without top-notch security, it's like a house made of glass - beautiful to look at but easy to break.
Checkout The How-to Guide on Building Scalable Website Application
Best Practices for Secure Development
Secure web application development isn't just about coding; it's an encompassing strategy that starts way before the first line of code is written and continues long after launch.
1. In-depth Security Planning:
Every great application starts with a plan. Factor in security from day one. Define potential threats, understand the kind of data your application will handle, and build a security blueprint.
2. Clean and Consistent Coding:
The code forms the backbone of any application. Utilize universally recognized coding practices and maintain a neat codebase. This ensures any developer, even those who join the project later, can easily identify and rectify potential vulnerabilities.
3. Prioritize Input Validation:
Don't trust any data entering your system. Whether it's from a user or another application, always validate inputs. Proper input validation can shield against a majority of common attacks.
4. Strong Authentication Protocols:
Always keep user data safety at the forefront. Introduce multi-factor authentication, biometric verifications, or CAPTCHA tests. And remember, passwords should never be stored in plain text.
5. Effective Session Management:
Sessions are a hacker's playground if not managed right. Use encrypted tokens, ensure they expire, and always keep them rotating to stave off session-related vulnerabilities.
6. Regular Monitoring and Testing:
Security isn't a one-time thing. Continuously monitor the application, perform penetration testing, and conduct code reviews. Automated tools are great, but manual reviews bring the human element of unpredictability.
7. HTTPS Everywhere:
Data protection isn't just about storage; it's about transmission, too. Secure data both in rest and in transit. HTTPS isn't a luxury; it's a necessity.
8. Educate and Train Your Team:
A well-informed team is your first line of defense. Regularly train your developers on the latest threats and best practices to tackle them, including the implementation of tools like the Chrome or Firefox VPN extension for enhanced online security. Consider investing in elearning video production and developing training programs to make it easier for developers to learn and retain information.
By weaving security into the fabric of your development process, you ensure a sturdy and reliable application that isn't just functional but also safe. Remember, it's easier to build security in from the start than to bolt it on later. Consider using an email builder to regularly share security updates and best practices with your team, reinforcing a proactive approach.
Explore the 10 Different Types of Web Applications & Their Uses
Common Web Application Vulnerabilities
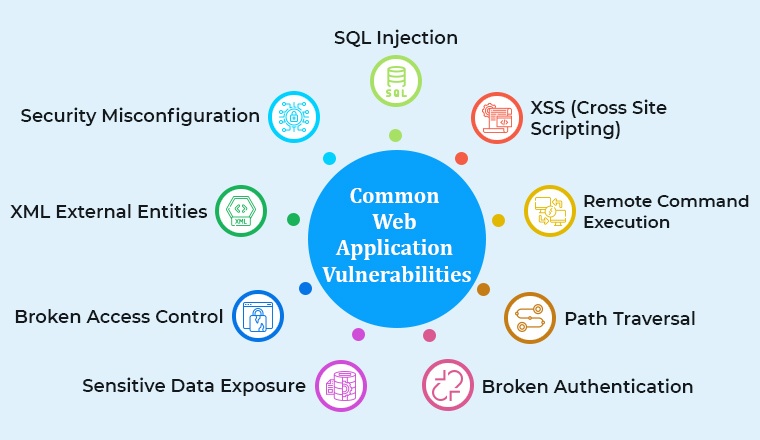
No matter how sleek, web apps are always on hackers' radar. Why? Because they're filled with vulnerabilities. Let's look into the most frequent threats you might encounter and the impact they can have.
- SQL Injection (SQLi): This is where attackers can sneak malicious code into your database through flawed application design. Think of it as a burglar finding an unlocked backdoor to your home. The result? Unauthorized access to your sensitive data.
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages viewed by users. This way, they can steal info or even change how your website looks. Kinda like someone scribbling over your favourite photo!
- Cross-Site Request Forgery (CSRF): In this sneaky method, attackers trick users into executing actions without them knowing. Imagine a stranger making purchases using your online shopping cart without you realizing it.
- Security Misconfigurations: Think of this as leaving your keys under the mat. Attackers find and exploit default configurations, incomplete setups, or overly verbose error messages to gain unauthorized access.
Which security mechanism is the least effective against common web application attacks?
The least effective security mechanism against common web application attacks is relying solely on client-side validation. This method is vulnerable as attackers can easily bypass it, modifying data or injecting malicious code, making the application susceptible to various attacks like Cross-Site Scripting (XSS) and SQL Injection.
The truth is these vulnerabilities can lead to serious issues. We're talking about data breaches, financial loss, or even damage to your reputation. So, stay alert, stay informed, and always prioritize your web app's security!
Read More on 13 Best Practices to Secure Microservices Architecture
Web Application Security Tools
Securing your web application isn't a one-and-done affair. It's an ongoing commitment. The good news? There's a slew of tools available to make your job easier.
- Static Analysis Tools: These examine code without running it. Think of them as proofreading a book for errors before publishing.
- Dynamic Analysis Tools: Now, think of reading a book out loud. These tools evaluate your web application as it runs, identifying live issues.
- Penetration Testing Tools: These are the secret agents of the web security world. They mimic cyber-attacks on your application, showing you where the weak points are.
- Web Scanners: Automated tools that scout for vulnerabilities. They're like guards constantly patrolling your application's perimeter.
- Open Source Security Tools: Courtesy of communities who care about safe web spaces, these are often cost-effective and updated by enthusiasts. OWASP, for instance, offers several tools that can help detect and mitigate potential threats in applications.
How can I protect my web application from security threats
There are several measures you can take to protect your web application, including:
- Using secure coding practices
- Input validation and sanitization
- Implementing proper authentication and authorization mechanisms
- Regularly updating and patching software
- Using HTTPS encryption
- Employing security testing and vulnerability scanning
What is the open web application security project (owasp)?
The Open Web Application Security Project (OWASP) is a nonprofit organization focused on improving software security. It provides free resources, tools, and community-driven documentation to help organizations identify and mitigate security risks in web applications. OWASP is best known for its "Top Ten" list of critical web application vulnerabilities.
Remember, tools are only as good as the strategy behind their use. Regularly update them, understand their strengths, and, more importantly, don't solely rely on them. Your human insight is just as crucial.
Regular Security Audits and Assessments
Regular checks on your web application aren't just a good idea; they're a must. The realm of web security constantly evolves, with new threats emerging almost daily. Here's why continuous monitoring and regular assessments are essential:
The Necessity of Continuous Monitoring
Web applications can be compromised in the blink of an eye. Without ongoing monitoring, you might miss a vulnerability until it's too late. Regular oversight keeps threats at bay and ensures that security patches are up-to-date.
Checkout 9 Responsive Web Design Principles You Should Know in 2023 and Beyond
Steps for Successful Audits and Assessments
- Identify and Prioritize Assets: Know what parts of your application are most critical.
- Conduct Regular Scans: Use security tools to scan for vulnerabilities frequently.
- Review Code: Periodically review your application's code to ensure that there are no security loopholes.
- Train Your Team: Keep your development and security teams informed about the latest threats.
- Act on Findings: After each assessment, take prompt action to address any discovered vulnerabilities.
By dedicating time to regular audits and continuously monitoring your application, you're protecting your business and ensuring a safer experience for your users. The web might be vast and unpredictable, but with diligent checks, your application can stand strong against threats.
User Education and Awareness
Educating users is crucial in amplifying web application security. Informed users become a formidable first line of defense against looming threats. Here's how you can enhance web security through user education:
Promote Security Awareness:
Drive home the point about the security risks associated with web applications. Highlight the prevalence of phishing scams and social engineering attacks, which aim to deceive users into revealing sensitive data or installing harmful software.
Spotting Phishing and Scams:
Train users to identify signs of phishing emails or messages. This includes scrutinizing sender details, looking for unusual requests, and avoiding clicking on suspicious links.
Password Policies:
Advocate for strong password creation and regular updates. Remind them of the risks of using the same password across multiple accounts.
Safe Browsing Habits:
Share insights on secure online habits, like refraining from using public Wi-Fi for confidential tasks and learning to recognize safe websites.
Staying Updated:
Stress the importance of software and system updates. Such updates often address and rectify known security gaps.
With the right knowledge, users can actively combat cyber threats, reinforcing technical measures with vigilant human intervention. It's essential to remember that security isn't just about tools; the human element is equally pivotal.
Conclusion
In today's fast-paced online space, the need for top-tier web application security is indisputable. We've explored the common vulnerabilities that plague many applications and emphasized the essential tools and best practices to counteract them. Regular security audits, an emphasis on user awareness, and proactive measures during development stages are pivotal for optimal safety.
Yet, security isn't just about the right tools or practices; it's about partnering with a team that prioritizes it at every phase. At SayOneTech, a leading web application development firm, our commitment to your security goes beyond just code. Our decade of experience isn’t just about building powerful web applications; it's about ensuring they stand strong against evolving threats.
If you're looking for a team that takes web application security as seriously as you do, consider giving us a shout. Your secure digital future might just start a conversation with us.
Share This Article
Subscribe to Our Blog
We're committed to your privacy. SayOne uses the information you provide to us to contact you about our relevant content, products, and services. check out our privacy policy.


